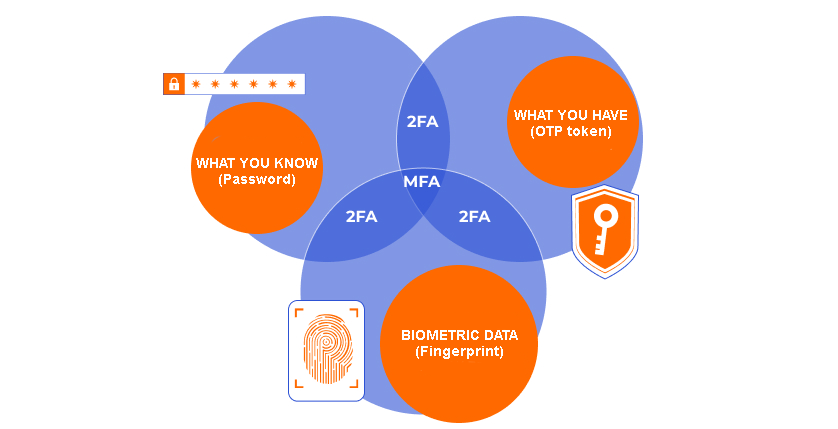
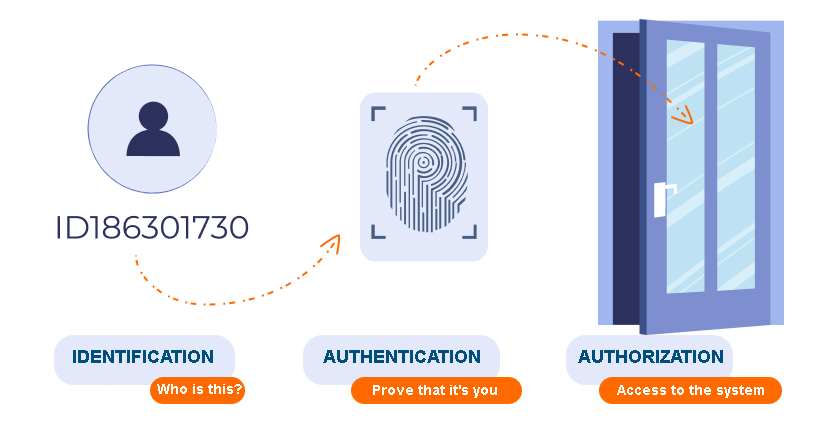
There are three concepts to explain access control in cybersecurity: identification, authentication, and authorization. Although these terms are closely related, they have differences that need to be clarified in order to have a good understanding of the correct terminology.
Before explaining what identification, authentication, and authorization mean, we should first define two other fundamental access control terminologies: subject and object.
A subject is an active entity that has access to an object. In the example of user access to a file, the subject is the user. However, the subject does not have to be a living entity, it can also be a program or process that accesses the object.
An object is a passive component that a subject has access to. Files, printers, computers, and databases are examples of objects in an access control mechanism.